In my previous article, I described an authentication method, where an ADFS Server is responsible for authenticating users. I also described which certificates are needed and how to properly export a certificate, so you can import it to you SharePoint Server.
ADFS Server Settings
When configuring the trust between your SharePoint Server and ADFS Server, the process is split into two parts:
- Establishing the trust by exchanging certificates.
- Establishing the relying party trust.
I will describe the process of establishing a trust between SharePoint Server and ADFS Server in a future article.
Relying Party Trust
The ADFS Server is responsible for authenticating users. SharePoint is an application that relies on ADFS to make sure that users are appropriately authenticated. Besides SharePoint, ADFS must also know that the incoming request is coming from a trustworthy application/website. This is established with a relying party trust.
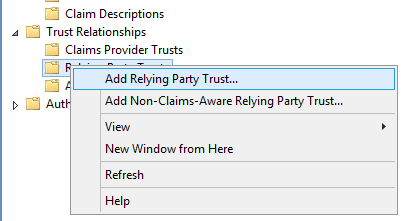
If we want to add a new partner, we right click on the Relying Party Trust folder and select the Add Relying Party Trust option. In the wizard that opens up, we fill in the required information that ADFS uses to make sure the request is coming from a SharePoint Server and from the underlying application.
Select Data Source
In the second part of the wizard, we need to select our data source that relies on the ADFS Server. Because in our case, the data source is SharePoint, the option we need to select is “Enter data about the relying party manually”. By clicking the next button, we move to the next step.
Specify Display Name
In this step, we enter a unique, descriptive name, so we will recognize the name of our data source in the future.
Choose Profile
In this step, we select the ADFS profile and move on to the next step.
Configure Certificate
In this step, we don’t need to perform any actions, so we can just press next.
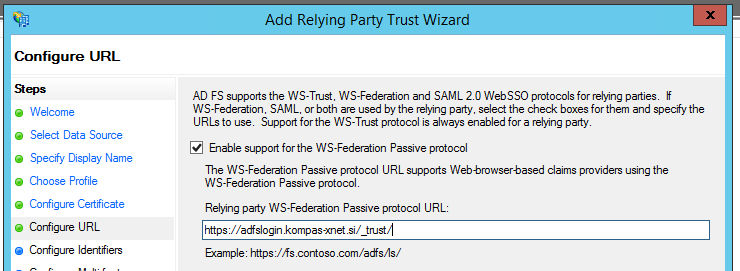
Configure URL
In this step we need to configure two things:
- Select the “Enable support for the WS Federation passive protocol” option.
- Into the “Relying party WS Federation Passive protocol URL” field, we need to enter the URL of the web application, which will use ADFS for authentication. Next to the URL, we need to add “/_trust/“.
In our case, the URL is as follows: https://adfslogin.kompas-xnet.si/_trust/
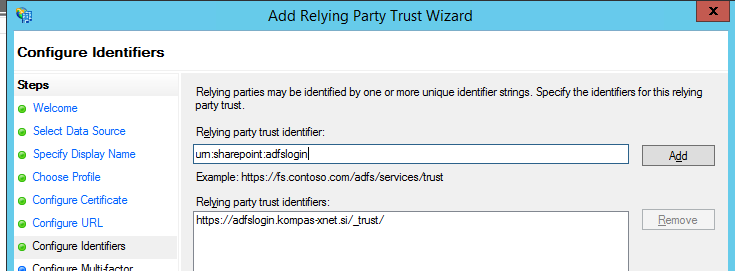
Configure Identifiers
In this step we need to add a new entry. The entry must uniquely identify the web application which will connect to the ADFS Server. We must specify the same identifier on the SharePoint Server, but more on that in a future article.
Configure Multi-Factor Authentication
In this step, we don’t need to specify anything.
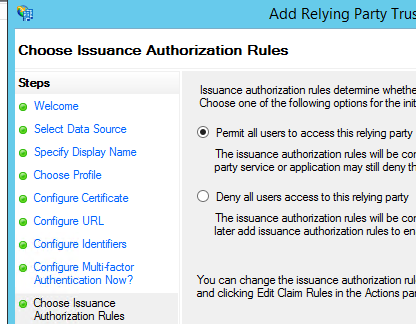
Choose Issuance Authorization Rules
In this step, it is very important that we select the “Permit all users to access this relying party” option.
Ready to Add Trust
In this step, we click next.
Finish
Even though this step is the last one in the wizard, we are not finished yet. We have the option to “Edit the Claims Rules Dialog for this relying party trust when wizard closes”.
A window called “Edit Claims Rules” will show up, enabling us to change what type of data users will use to identify.
Edit Claims Rules
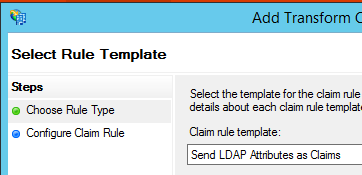
By clicking the Add rule button, a wizard starts up which we use to specify where will ADFS authenticate the user. For AD users, we need to select “Send LDAP Attributes as Claims” and in the next step we specify what are the attributes that describe a user.
“Configure Claims Rule” defines what the name of the rule will be, what type of “Attribute store” do we have, where we set “Active Directory” and configure the mapping of Outgoing and AD attributes.
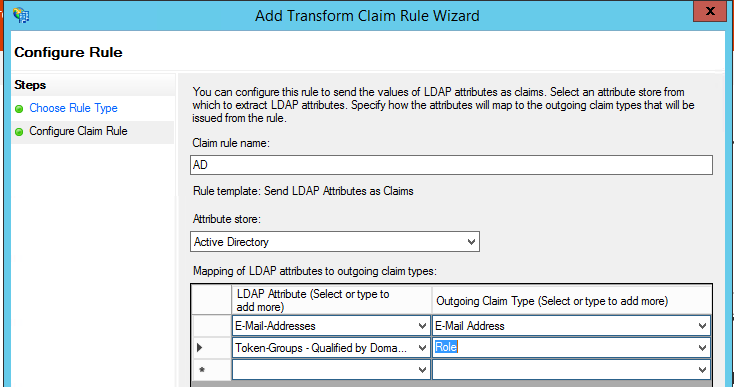
In this step, we must always select at least two types of mapping. The first one usually uniquely describes the user. Most often this is the user’s email and Outgoing Claim E-mail Address. Due to the fact that some users may not have a valid e-mail address, you can also set the User Principal Name as the identifier.
The second option is the one that usually defines AD groups a user is a member of. Mapping must be set to “Outgoing Claim Type: Role”.
When everything is set up, we can save the rules and that is everything we need to configure on the ADFS Server.
In the next article, I will describe what needs to be configured on SharePoint in order to guarantee successful authentication with the ADFS Server.